An asset is any data, device or other component of the environment that supports activities related to information, these assets include hardware, software and sensitive information of companies and must be protected from illegal access, alterations, theft, disclosure, etc.
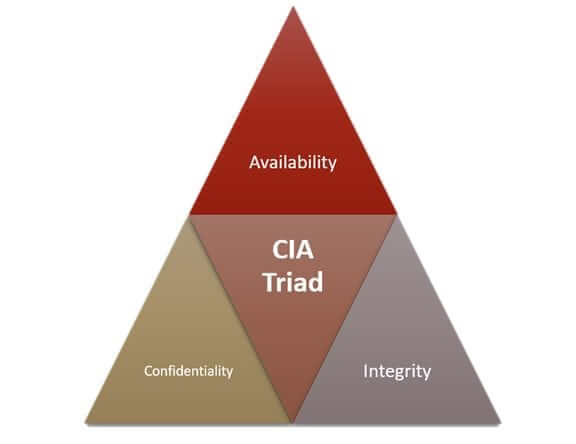
The main objective of the CIA TRIAD is to secure assets in three main security components, the so-called security triangle; Confidentiality, Integrity and Accessibility.
These 3 concepts depend perfectly on each other, then we explain how each of these security aspects works.
Confidentiality:
Confidentiality Ensures that access to information is by the persons indicated in their three states: storage, process and transit.
A breach of confidentiality is not always derived from the actions of cyber attackers, many times it may be due to failures in the security mechanisms implemented, in the definition and knowledge of the organization's security policies or configuration failures.
Confidentiality is also affected due to human errors, so different mechanisms must be chosen to grant this property to information such as authentication, access control and data encryption among others.
Integrity:
Integrity must ensure that the information has not been modified during its process, storage or transit.
Integrity must be analyzed from 3 perspectives:
Prevent someone with modification permissions from making a mistake and modifying the data.
Prevent someone without modification permits from making any changes.
Prevent any program or application that interacts directly with the "objective" information make any changes.
Availability:
The availability of the information refers to keeping active access to the necessary information to those who must have access to it at the time it is necessary.
We can use some methods to achieve this, such as:
Implement redundant solutions
Backup schemes
Business Continuity Process (BCP) and Disaster Recovery Process (DRP) plans, which must be periodically tested to ensure proper operation.
These three information security properties depend on each other as follows; If there is no confidentiality, the integrity of the information is probably violated, giving rise to the fact that some unauthorized person can modify the information, if this happens, the business information or applications will be affected in an impact on the availability of that information.
In this way, Confidentiality, Integrity and Availability become the main gear for the security of all information, where if any of the elements fails, it impacts others.
Most organizations use the “TRIAD†to review the security mechanisms available to the applications they use, all with the objective of minimizing risks. “It is not about using one or the other, but all in a balanced wayâ€.