IT assets are the technological resources that every company has to streamline its management and are used to achieve business objectives, and are divided into tangible and intangible assets (hardware and software).
Asset management in IT is focused on both hardware and software, ensuring that the organization has the ability to manage these assets throughout their life cycle. In the case of the software, it must be ensured that the licenses of the programs are fulfilled.
The classification of IT assets helps us greatly in the valuation and protection of IT assets, it also includes all the processes and procedures for reclassification, since after a period of time the information considered sensitive can decline in value or criticality.
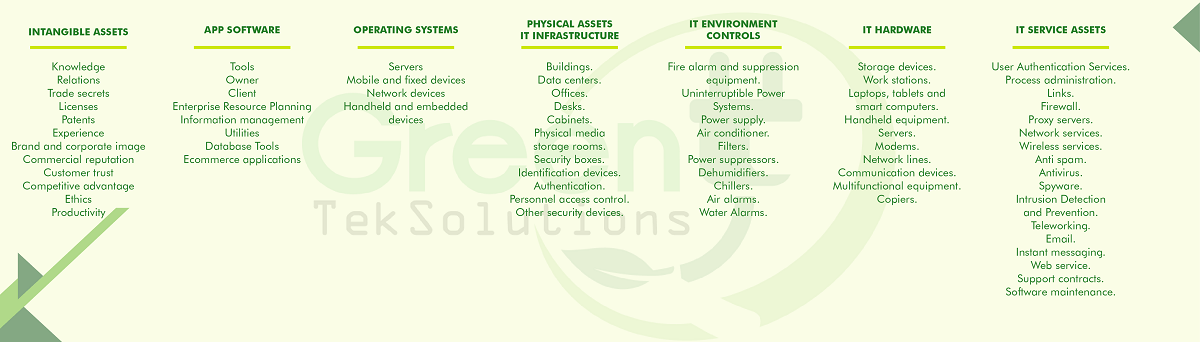
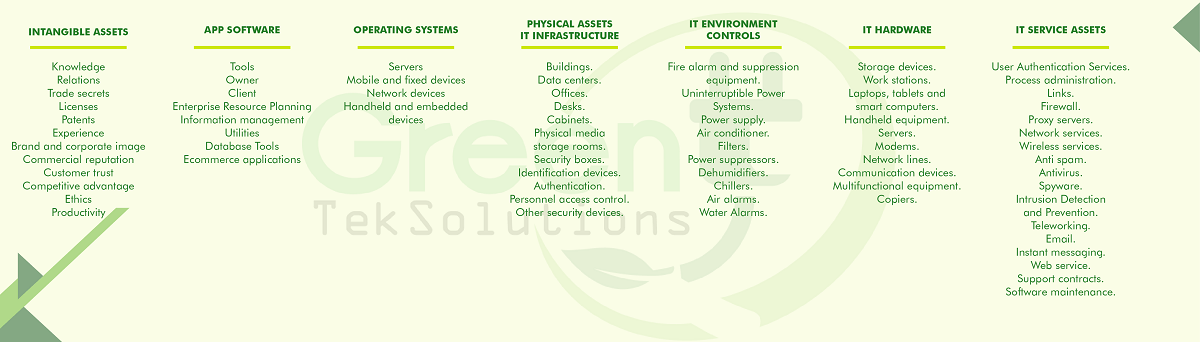
This could be an appropriate classification of assets within a company.
Identity theft due to lack of classification and proper disposal of IT assets is an important issue when it comes to security, which is why the sanitization of assets according to their life cycle must be included.
Risks of not sanitizing the data
When the information is not deleted safely, important information can remain within the devices, which can lead to probable risks such as:
- Theft of private or personal data of customers or employees.
- Theft of critical data can be recovered and used by adversaries or competitors.
- Leakage of private or personal data resulting in large fines and legal actions for organizations, for not complying with personal data protection laws.
- Intellectual property can be recovered and published, resulting in loss of reputation and / or profits.
Reasons to sanitize
Some of the reasons why it is required to sanitize the storage media are:
- Reuse: to relocate the device to a different user or use it for another purpose.
- Resell: to resell the device that already has our personal data, especially if they are identifiable.
- Repair: When it has to be repaired, but it has sensitive personal information.
- Remove: When discarding or donating, unsubscribe the device.
- Destroy: When confidential information is available, which requires that the devices be physically destroyed.
- Regulatory: For compliance with regulations of law for the protection of personal data.
There are currently several organizations that have donation or recycling programs for electronic devices that include cell phones, laptops, servers, video game consoles and tablets.
In the country, the most common services offered for the physical destruction of documents and physical devices (magnetic disks) are demagnetization, crushing and incineration.
But they are not all the methods that you can and should use, you should always keep in mind to perform a sanitization properly and respecting the environment.