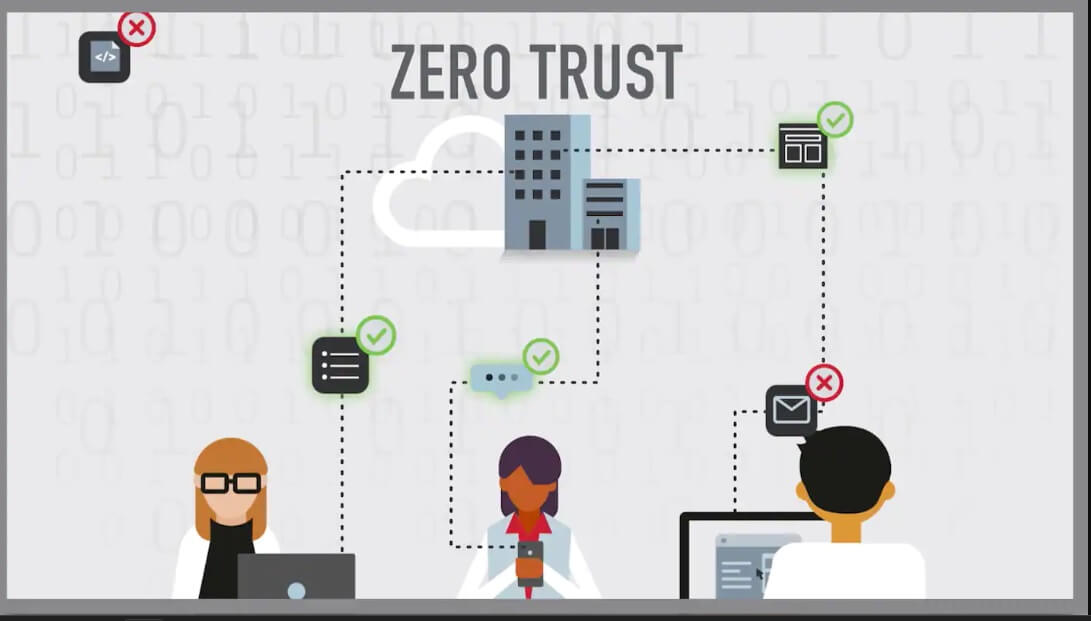
The Zero Trust Model is an approach to cybersecurity that assumes that a network or system should not be trusted by default, even if it is within the organization's perimeter.
Adopting a Zero Trust Model can help businesses of all industries and sizes improve their overall security posture, reduce the risk of security incidents, and ensure compliance with regulatory requirements.
The Zero Trust Model is based on several key principles, including:
- Verifcation: Every user and device must be authenticated and verified.
- Limit access: Access should only be given to users on a "need-to-know" basis, and they are only allowed to consult some specific resources.
- Monitor all activity: All activity should be monitored and logged to detect suspicious or unauthorized behavior.
- Assume breach: Businesses should assume their network has already been compromised (even if not) and implement strict measures to detect and react to breaches quickly.
- Encrypt everything: Every single piece of data should be encrypted to ensure it cannot be intercepted or stolen.
However, implementing a Zero Trust Model requires significant planning, investment, and significant changes through every stage of the organization, so be patient and take your time to make all the necessary adjustments.
It is time to look forward!!
With decades of experience helping businesses protect themselves, the environment, and their data, GreenTek Solutions is ready to solve all your IT requirements. From professional data destruction to IT Asset disposition, we offer a wide range of services that meet both your budget and requirements.