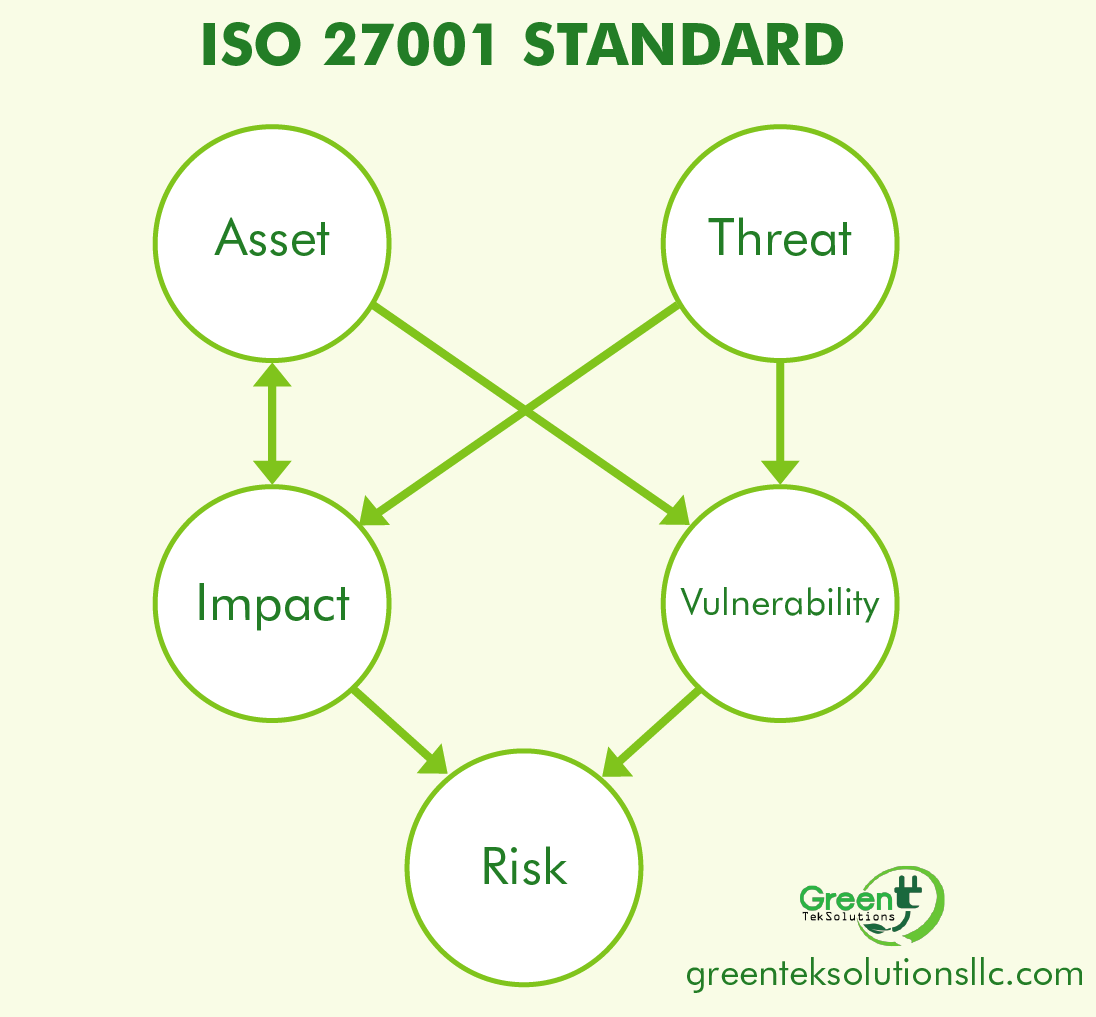
The assets are the resources of the ISO 27001 Information Security System, necessary for companies to function and achieve the objectives set.
ISO 27001 is an international standard that allows the assurance, confidentiality and integrity of data and information, as well as the systems that process it.
The ISO 27001: 2013 standard for Information Security Management Systems (ISMS) allows organizations to assess the risk and apply the necessary controls to mitigate or eliminate them.
The application of ISO-27001 means a differentiation from the rest of the companies, which improves the competitiveness and image of an organization.
Information Security Management is complemented by good practices or controls established in ISO 27002.
The assets are directly or indirectly related to all the entities of the company according to their function as the following scheme.
Structure of ISO 27001
- Purpose and scope: The standard begins by providing guidance on the use, purpose and mode of application of this standard.
- Normative References: Recommends the consultation of certain documents essential for the application of ISO27001.
- Terms and Definitions: Describe the terminology applicable to this standard.
- Context of the Organization: This is the first requirement of the standard, which includes indications about the knowledge of the organization and its context, the understanding of the needs and expectations of the interested parties and the determination of the scope of the Security Management System of the information.
- Leadership: This section highlights the need for all employees of the organization to contribute to the establishment of the standard. For this, senior management must demonstrate their leadership and commitment, develop a security policy that knows the entire organization and assign roles, responsibilities and authorities within it.
- Planning: This is a section that highlights the importance of determining risks and opportunities when planning an Information Security Management System, as well as establishing Information Security objectives and how to achieve them.
- Support: In this clause, the rule states that for the proper functioning of the ISMS, the organization must have the resources, competencies, awareness, communication and relevant documented information in each case.
- Operation: To comply with the Information Security requirements, this part of the standard indicates that the organization's processes must be planned, implemented and controlled, an assessment of the Information Security risks and an adequate treatment of they.
- Performance Evaluation: This section establishes the need and way to carry out the monitoring, measurement, analysis, evaluation, internal audit and review by the management of the Information Security Management System, to ensure It works as planned.
- Improvement: In the tenth section of the standard, there are the obligations that an organization will have when it finds a nonconformity and the importance of continuously improving the convenience, adequacy and effectiveness of the ISMS.
Asset environment failures
The failures that occur in the assets of the environment are:
- Cause information systems failures
- Cause information failures
- Support functionalities of the organization
- Conditioners of other assets